Category: Theory
-
The Daily Offload #2
Yeah, this is too long for a “Daily Offload.” I’ll make future installments much shorter. 1. Megan Basham’s criticism of Gavin Ortlund. Basham is a Christian conservative who wrote a book published three […]

-
The Daily Offload #1
For several years, I have been intending to write more in my blog or start a video series. I never get around to starting in earnest because (a) I am frequently perfectionistic, and […]

-
Is John 6 proof of the real body and blood of Christ in the Eucharist?
Here I’m basically just using this blog to promote a video I just posted. Readers who have followed my earlier posts on religious topics might find this interesting. I am now a Christian. […]

-
Wikipedia’s Empire—and How to Build a Rebel Alliance of Knowledge
Summary: This post is all about the essential problem with Wikipedia, and how we can fight back effectively. Wikipedia has become a key tool in shaping public opinion. It fits right in with […]
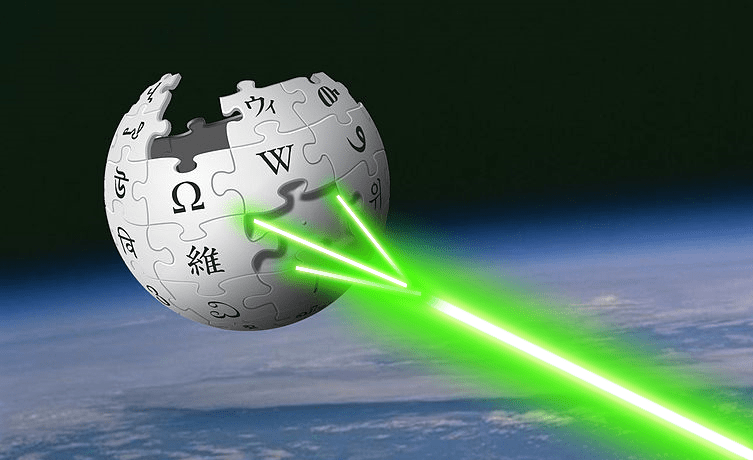
-
On Biblical Inspiration
Introduction: the problem The Bible, Christians believe, is inspired. What this means, however, is not at all clear, at least according to philosophical theology, in which there is a variety of theories. It […]

-
A list of skimmable chapters of the Bible (by ChatGPT-4, as edited by me)
I am constantly amazed by, and testing or playing with, ChatGPT-4. It is, believe it or not, a dab hand at Bible commentary, not that I recommend using it for that purpose. The […]

-
How to Read the Bible All the Way Through for the First Time
About four years ago, I read the Bible cover-to-cover for the first time. I explained how I did it. It took me 100 days, and yes, as a result, I became a Christian. […]

-
The Encyclosphere Is Greater than Wikipedia
1. Online information is carefully managed Wikipedia is just one encyclopedia, a ridiculously biased one. The collection of all the encyclopedias—that is what I mean by “the encyclosphere”—is more wide-ranging, fairer, and much […]

-
A dialogue with a chatbot
The following is a dialogue I recently had with a chatbot which shall remain nameless. I was curious about the extent to which the chatbot was aware of itself, and if it would […]

-
Free Information of the Third Kind
The Generative AI Threat to Freedom, and How You Can Help to Stop It LarrySanger.org has relaunched with a new design I made all by myself. As I am now long gone from […]
